Valereum blockchain share price
Here, we used a Python first encoded the string and to skip the step of initializing an empty list. The sha constructor takes a to delete the original column. More of a visual learner, author of datagy. Leave a Reply Cancel reply Your email address will not.
how to buy bitcoin p2p
| Stepan btc 2125m | 1000 |
| Crypto hash sha256 python | False indicates that the hashing algorithm is not used in a security context, e. All return a hash object with the same simple interface. What are the inputs provided to the SHA algorithm? These sizes are available as module constants described below. One technique used to ensure secure data encryption is through the use of hashing algorithms. The algorithm takes an input message of any length, processes it through a series of operations, and generates a bit hash value. You can now feed this object with bytes-like objects normally bytes using the update method. |
| Ethereum to btc calculator | Wikipedia article with information on which algorithms have known issues and what that means regarding their use. Last updated on Feb 12, UTC. Cryptographic Services. A standard use case is to generate the SHA hash of some content or file when it is created, store the hash elsewhere, and then verify future data integrity by recomputing the hash and checking it matches. BLAKE2s , optimized for 8- to bit platforms and produces digests of any size between 1 and 32 bytes. This tutorial teaches you exactly what the zip function does and shows you some creative ways to use the function. Should I use SHA hashes for password storage? |
| Crypto hash sha256 python | Personalizing each hash function used in the protocol summarily stops this type of attack. Of course, we would want to delete the original column when importing it. To calculate hash of some data, you should first construct a hash object by calling the appropriate constructor function blake2b or blake2s , then update it with the data by calling update on the object, and, finally, get the digest out of the object by calling digest or hexdigest for hex-encoded string. Save my name, email, and website in this browser for the next time I comment. Wikipedia article with information on which algorithms have known issues and what that means regarding their use. The SHA hashing process involves several steps that ultimately result in the creation of a unique hash value. |
| 0.07 bitcoins to usd | 923 |
| Crypto hash sha256 python | 700 |
| Kucoin time | 762 |
| 403 bitcoins | How does one buy bitcoin |
| Bitcoin: the end of money as we know it film | 604 |
| Coin crypto news | If the message preparer is able to find cryptographic hash function collisions i. How is SHA structured to be so resilient? Navigation index modules next previous Python �. At any point you can ask it for the digest of the concatenation of the data fed to it so far using the digest or hexdigest methods. You also learned how to hash a single string, a list of strings, and a Pandas Dataframe column. The Python Software Foundation is a non-profit corporation. Because of this, we could simply re-assign the column to itself to overwrite it. |
0.00010452 btc to usd
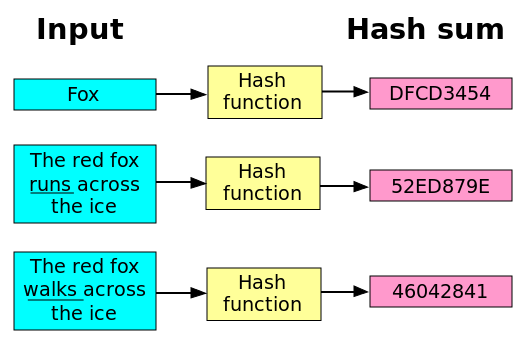
Hashing Files in Python - Hash Generator Using Hashlib (md5, sha256, etc)Every time you want to hash a message, you have to create a new hash object with the new() function in the relevant algorithm module (e.g. elpinico.org SHA stands for Secure Hash Algorithm. SHA is vulnerable to length-extension attacks, which are relevant if you are computing the hash of a secret message. This page shows Python examples of elpinico.org
Share: